Notes
quartz.config.tsplugins: { transformers: [ Plugin.Latex({ - renderEngine: "katex", + renderEngine: "mathjax", }), ] }.
.gitmodules[submodule "content"] path = content url = git@github.com:Nasr-905/content.git.
Image Pre-processing def pre_process_image(image_path, contrast_factor=1.5): # Load image image = Image.open(image_path).convert("RGB") # Increase contrast ...
quartz.config.tsplugins: { transformers: [ + Plugin.Staticrypt(), ] }.
quartz.config.tsconfiguration: { - pageTitle: "🪴 Quartz 4.0", - pageTitleSuffix: "", + pageTitle: "❯ NAS", + pageTitleSuffix: " | NAS", ...
.gitignore+ .env .env+ GOATCOUNTER_WEB_ID='cerebrum-secundum' quartz.config.ts+ import 'dotenv/config'; + const myGoatCounterWebID = process.env.GOATCOUNTER_WEB_ID ...
quartz.config.tsplugins: { transformers: [ + Plugin.Image(), ] }.
This feature allows for comments to be applied to this website. Setting Up the Back-end Setting Up the Front-end quartz.config.tsplugins: { transformers: [ + Plugin.Remark42({ + host: "remark.nasrudeen.com", + site_id: "remark", + // components: Array<String>, + // max_shown_comments: number, + // max_last_comments: number, + // theme: 'light' | 'dark', + // page_title: string, // Don't use this, it'll break your comment database.
quartz.config.tsplugins: { transformers: [ + Plugin.TelescopicText(), ] }.
quartz.config.ts plugins: { emitters: [ + Plugin.TimelinePages({ + limit: 100, + }), - Plugin.FolderPage(), - Plugin.TagPage(), // Some Lines + Plugin.TimelineFolderPage(), ...
Install Stable build on Linux with pip for python and cpu compute platform pip3 install torch torchvision torchaudio --index-url download.pytorch.org/whl/cpu ...
Initial Model Training: Start with a small labeled dataset and train an initial model. Query Strategy: Use the model to predict on unlabeled data. Identify the most “informative” or “uncertain” data points (e.g., those the model is least confident about).
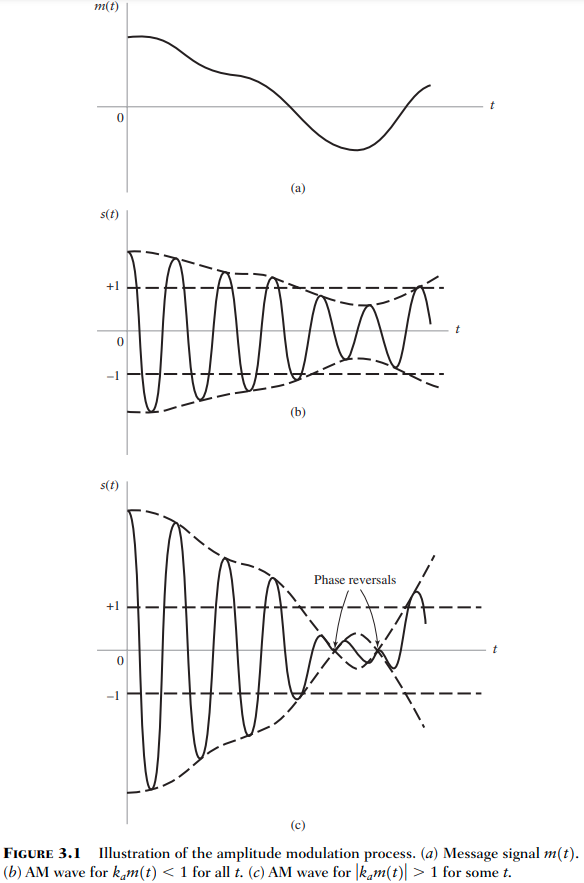
Amplitude-modulated Wave s(t) = A_c[1 + k_am(t)](2 f_c t) = [1 + k_am(t)]c(t) (3.2) m(t) is the message or information-bearing signal c(t) = A_c(2 f_c t) is the carrier wave A_c|1 + ...
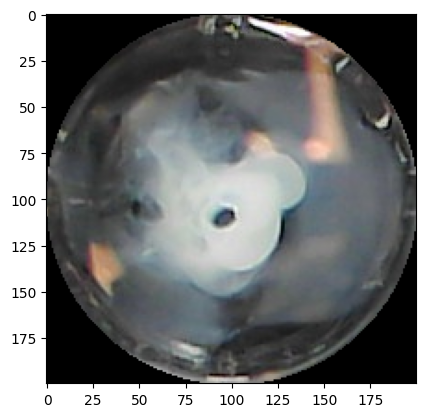
This is a method used to quantify circle-ness = }{}.
This is a method used to quantify circle-ness = }{^2}.
Creating a Worker Project npm create cloudflare@latest -- my-first-worker Then after choosing your options npx wrangler dev Depolying npx wrangler deploy ...
This is a method used to quantify circle-ness = ^2}{}.
Docker is a tool that makes it easy to run applications in isolated environments called containers. Think of it like this: 📦 A container is like a “portable box” that has everything an app needs to run (code, libraries, dependencies).
This is a method used to quantify circle-ness = {a^2}} Where: a is the length of the semi-major axis. b is the length of the semi-minor axis.
This is a method used to quantify circle-ness Fourier descriptors are derived from the Fourier transform of the shape’s boundary. If the boundary is represented as a complex signal (z(t) = x(t) + iy(t)), the Fourier descriptors (a_n) are given by: a_n = {N} _{k=0}^{N-1} z(k) e^{-i {N}} where: N is the number of boundary points.
Git submodules are essentially nested git repositories where the parent repository references the child repository **as a pointer to a specific commit of the child repository ** ...
Checkout This checks out a given commit, branch or tag and by doing so, git updates the files in your working directory to match the commit/branch/tag. ...
Paragraphs are separated by a blank lines. One Paragraph. Another paragraph. One Paragraph. Another paragraph. White-space collapsing. Multiple adjacent spaces and multiple newlines between paragraphs.
title: Title of the page. If it isn’t provided, Quartz will use the name of the file as the title. description: Description of the page used for link previews.
Install pip install <package-name> Uninstall pip uninstall <package-name> Version Check python3 >>> import <package-name> >>> print(<package-name>.__version__) ...
They’re good for allowing some projects to simulate having their own dedicated setup (computer). So that: You don’t need to give the program admin permissions.
This is a method used to quantify circle-ness = }{}.
Transfer learning involves taking a model pre-trained on a large, general dataset (e.g., ImageNet) and adapting it to a new, specific task or domain (e.g., gel formation analysis) ...
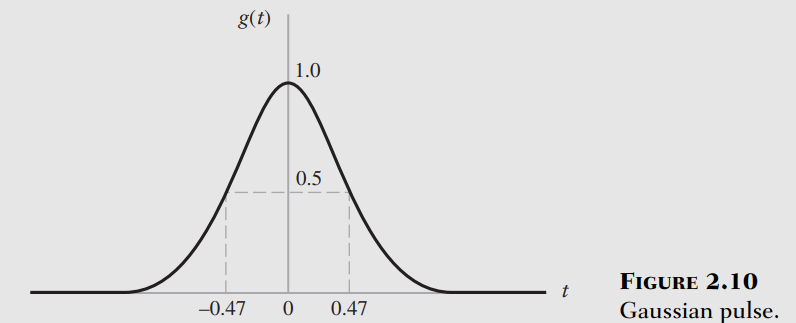
(t) = 0 t 0 and _{-}^ (t)dt = 1 Sifting/Replication Property _{-}^ g()(t - )dt =g(t)*(t)= g(t) (2.63) Fourier Transform (t) 1, 1 (f) Frequency Shifting Property (-j2 f_c t) (f-f_c) ...
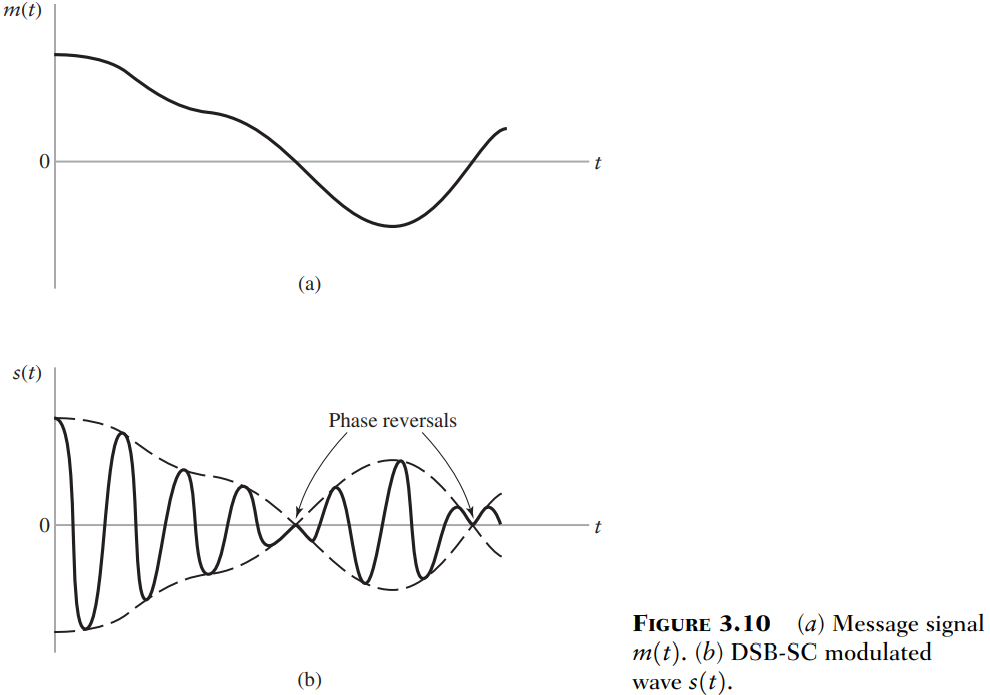
Transmitter Recall that AM is power and bandwidth inefficient, DSB-SC attempts to be more power efficient. Note: Similar to AM, bandwidth of the message for DSB-SC (W) is expected to be much smaller than f_c, that is: BW = W << f_c This is so that, in the frequency domain, when the cosine doubles the message, they don’t overlap The Envelope doesn’t follow the message Notice: We get phase reversals because the original message not everywhere positive, so the envelope (dashed line), doesn’t follow the message.
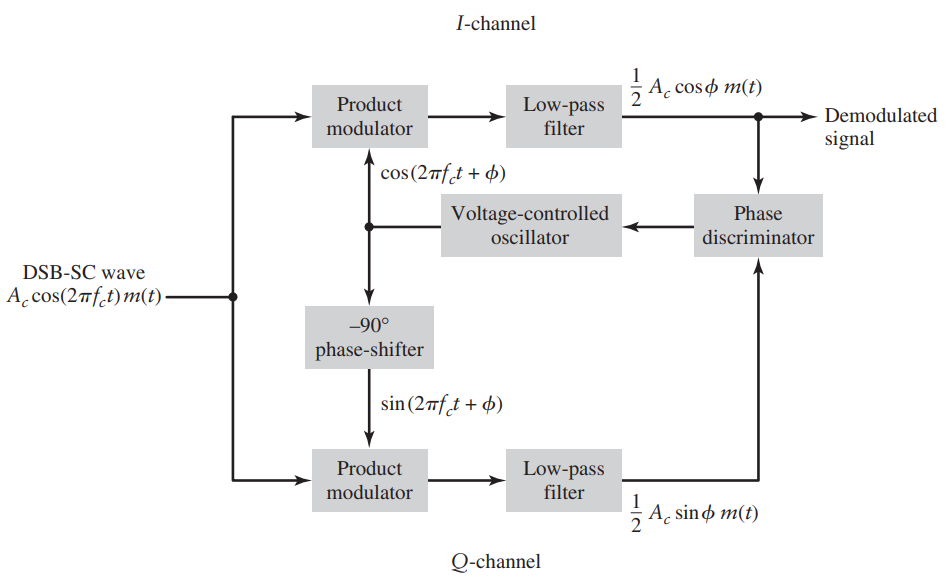
This receiver corrects for a changing phase shift in Double Sidebar Suppressed Modulation Recall that in the non-ideal case: We can also say: *Product modulator is just the multiplication ...
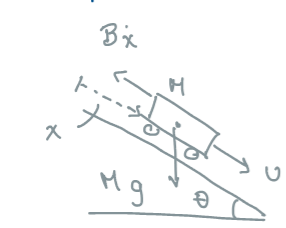
Example 1: Cruise Control of a Car u - Force imparted by the engine M - Mass of the car -B - Friction - Slope incline Governing Equation M = u + _{ d } - B Let y = to get a linear 1^{} order ordinary ...
Power Signal Signals where the following holds: _{T } {2T}_{-T}^T|g(t)|^2dt <.
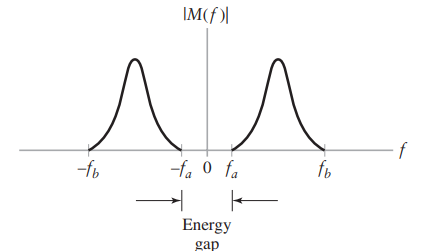
SSB Modulation attempts to be power efficient and bandwidth efficient, but it’s limited in use cases. It was originally designed for voice signals (telephones), this is because they have a unique structure with a small energy gap around 0 frequency.
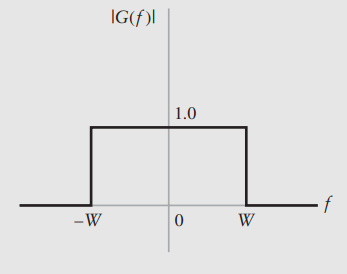
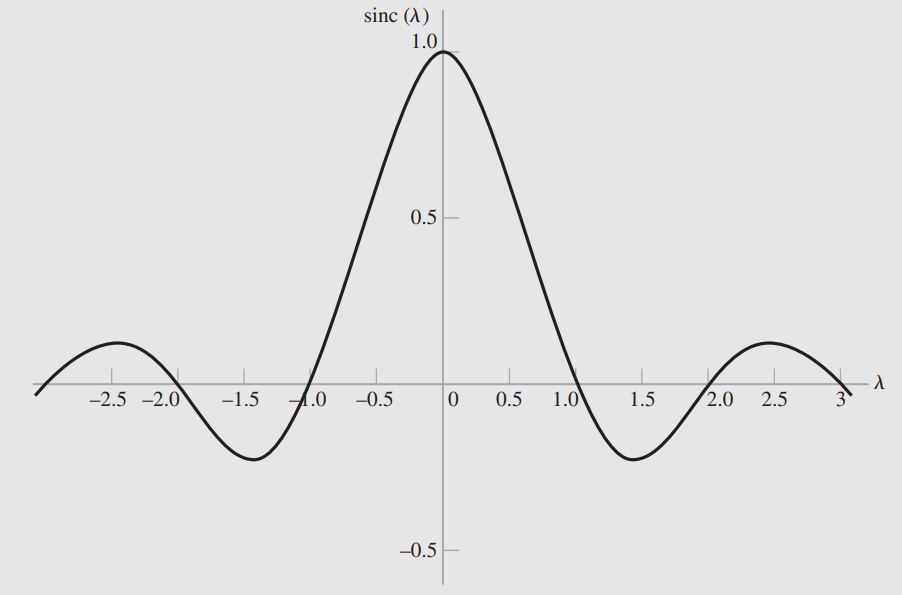
Strictly Limited in Frequency/Time A signal is strictly limited in frequency (also called strictly band limited) if outside a certain bandwidth, the Fourier Transform is exactly ...
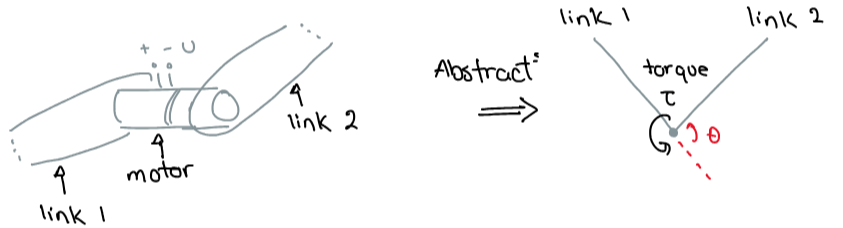
Say u - Voltage - Torque - Angle of link 2 relative to link 1 _d is the desired angle Goal What is u(t) so _d? Modelling We use a sensor to determine This block diagram model is called a ‘plant’ ...
Properties of The Fourier Transform Linearity (Superposition) Let g_1(t) G_1(f), g_2(t) G_2(f), then c_1, c_2 : c_1 g_1(t) + c_2 g_2(t) c_1 G_1(f) + c_2 G_2(f) (2.14) Proof From the ...
Fourier Transform (Analysis Equation) The Fourier transform will Uniquely define G(f) G(f) = \{g(t)\} = _{-}^ g(t) (-j2 f t) dt (2.1) For a non-periodic g(t) ...
Can perform semantic segmentation The ability to distinguish areas of the data Point Net Extracts both local and global features of a Point Cloud with any orientation Still not entirely ...